Hi,
I’m having issues with the parsing of journalctl, I’m working on a FedoraCoreOS box.
I followed the examples given here Journald | CrowdSec and ended up with
# acquis.yaml
---
listen_addr: 127.0.0.1:7422
appsec_config: crowdsecurity/appsec-default
name: CrowdsecAppSec
source: appsec
labels:
type: appsec
---
source: file
force_inotify: true
filenames:
- /var/log/caddy/*.log
labels:
type: caddy
---
source: journalctl
journalctl_filter:
- "_TRANSPORT=journal"
labels:
type: syslog
---
source: journalctl
journalctl_filter:
- "_TRANSPORT=syslog"
labels:
type: syslog
---
source: journalctl
journalctl_filter:
- "_TRANSPORT=stdout"
labels:
type: syslog
---
source: journalctl
journalctl_filter:
- "_TRANSPORT=kernel"
labels:
type: syslog
---
And the following podman quadlet
[Unit]
Description=Crowdsec Quadlet
[Container]
Image=docker.io/crowdsecurity/crowdsec:v1.6.11-debian
ContainerName=crowdsec
Network=tunnel.network
NoNewPrivileges=true
DropCapability=ALL
Environment="TZ=Europe/Paris"
Environment="BOUNCER_KEY_caddy={{ $CROWDSEC_CADDY_BOUNCER_API_KEY }}"
Environment="BOUNCER_KEY_firewall={{ $CROWDSEC_FIREWALL_BOUNCER_API_KEY }}"
Environment="ENROLL_KEY={{ $CROWDSEC_API_KEY }}"
Environment="USE_WAL=true"
Environment="ENROLL_INSTANCE_NAME=telstar"
Environment="COLLECTIONS=crowdsecurity/linux crowdsecurity/sshd crowdsecurity/caddy crowdsecurity/http-cve crowdsecurity/whitelist-good-actors crowdsecurity/appsec-virtual-patching crowdsecurity/appsec-generic-rules"
# TODO: Dunno if needed, instance is stored in config
Volume=/srv/vic1707/containers/crowdsec/data:/var/lib/crowdsec/data:Z,rw
# TODO: Dunno if needed, custom config is enough?
Volume=/srv/vic1707/containers/crowdsec/config:/etc/crowdsec:Z,rw
Volume=/home/vic1707/.config/containers/crowdsec/acquis.yaml:/etc/crowdsec/acquis.yaml:Z,rw
Volume=CrowdsecLogs.volume:/var/log:ro
Volume=/var/log/journal:/run/log/journal:ro
[Service]
Restart=always
ExecStartPre=/usr/bin/bash -c "until [ -f /run/restore-complete ]; do sleep 1; done"
ExecStartPre=/usr/bin/bash -c "until [ -f /run/user/1001/crowdsec-volume-ready ]; do sleep 1; done"
# needed by the bounder, I think
ExecStartPost=/usr/bin/touch /run/user/1001/crowdsec-ready
[Install]
WantedBy=default.target
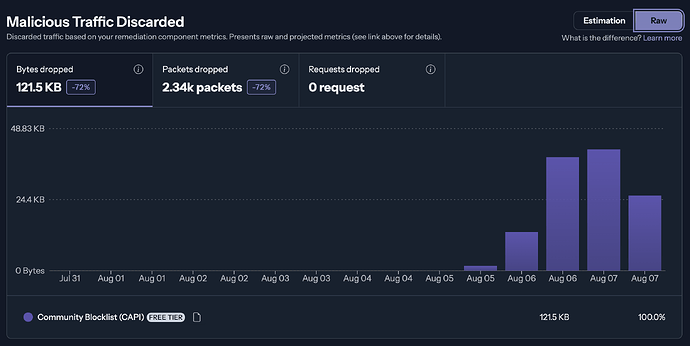
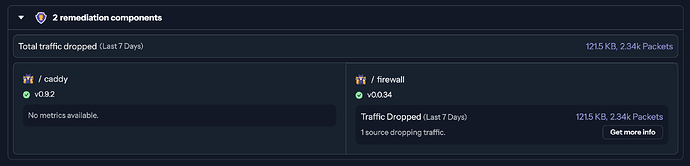
Things appear to be picked up by crowdsec nicely
vic1707@telstar:~$ podman exec crowdsec cscli metrics
+--------------------------------------------------------------------------------------------------------------------------------------+
| Acquisition Metrics |
+--------------------------------------------+------------+--------------+----------------+------------------------+-------------------+
| Source | Lines read | Lines parsed | Lines unparsed | Lines poured to bucket | Lines whitelisted |
+--------------------------------------------+------------+--------------+----------------+------------------------+-------------------+
| file:/var/log/caddy/access.log | 259 | 259 | - | 230 | - |
| journalctl:journalctl-%s_TRANSPORT=journal | 59.99k | - | 59.99k | - | - |
| journalctl:journalctl-%s_TRANSPORT=syslog | 6 | - | 6 | - | - |
+--------------------------------------------+------------+--------------+----------------+------------------------+-------------------+
+-------------------------------------------+
| Local API Alerts |
+-----------------------------------+-------+
| Reason | Count |
+-----------------------------------+-------+
| crowdsecurity/http-bad-user-agent | 1 |
+-----------------------------------+-------+
+------------------------------------------------------------------------------------+
| Bouncer Metrics (firewall) since 2025-07-27 16:46:31 +0000 UTC |
+----------------------------+------------------+-----------------+------------------+
| Origin | active_decisions | dropped | processed |
| | IPs | bytes | packets | bytes | packets |
+----------------------------+------------------+-------+---------+--------+---------+
| CAPI (community blocklist) | 15.00k | 2.49k | 48 | - | - |
+----------------------------+------------------+-------+---------+--------+---------+
| Total | 15.00k | 2.49k | 48 | 62.05M | 60.09k |
+----------------------------+------------------+-------+---------+--------+---------+
+-------------------------------------------------------------------------------------+
| Bouncer Metrics (firewall@10.89.0.6) since 2025-07-27 17:46:31 +0000 UTC |
+----------------------------+------------------+------------------+------------------+
| Origin | active_decisions | dropped | processed |
| | IPs | bytes | packets | bytes | packets |
+----------------------------+------------------+--------+---------+--------+---------+
| CAPI (community blocklist) | 14.98k | 14.58k | 238 | - | - |
+----------------------------+------------------+--------+---------+--------+---------+
| Total | 14.98k | 14.58k | 238 | 10.29M | 23.39k |
+----------------------------+------------------+--------+---------+--------+---------+
+-------------------------------------------------------------------------------------+
| Bouncer Metrics (firewall@10.89.0.8) since 2025-07-27 18:01:31 +0000 UTC |
+----------------------------+------------------+-------------------+-----------------+
| Origin | active_decisions | dropped | processed |
| | IPs | bytes | packets | bytes | packets |
+----------------------------+------------------+---------+---------+-------+---------+
| CAPI (community blocklist) | 21.34k | 410.04k | 7.67k | - | - |
| crowdsec (security engine) | 1 | 0 | 0 | - | - |
+----------------------------+------------------+---------+---------+-------+---------+
| Total | 21.35k | 410.04k | 7.67k | 1.99G | 4.52M |
+----------------------------+------------------+---------+---------+-------+---------+
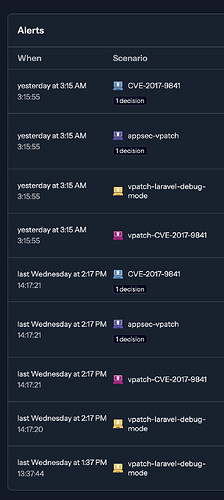
+---------------------------------------------------------------+
| Local API Decisions |
+-----------------------------------+----------+--------+-------+
| Reason | Origin | Action | Count |
+-----------------------------------+----------+--------+-------+
| ssh:exploit | CAPI | ban | 1057 |
| crowdsecurity/http-bad-user-agent | crowdsec | ban | 1 |
| http:bruteforce | CAPI | ban | 6786 |
| http:exploit | CAPI | ban | 2462 |
| ssh:bruteforce | CAPI | ban | 6184 |
| vm-management:exploit | CAPI | ban | 1 |
| generic:scan | CAPI | ban | 1324 |
| http:crawl | CAPI | ban | 49 |
| http:scan | CAPI | ban | 3642 |
+-----------------------------------+----------+--------+-------+
+---------------------------------------+
| Local API Metrics |
+----------------------+--------+-------+
| Route | Method | Hits |
+----------------------+--------+-------+
| /v1/alerts | POST | 1 |
| /v1/allowlists | GET | 5509 |
| /v1/decisions/stream | GET | 38556 |
| /v1/heartbeat | GET | 5508 |
| /v1/usage-metrics | POST | 551 |
| /v1/watchers/login | POST | 94 |
+----------------------+--------+-------+
+------------------------------------------------------------+
| Local API Bouncers Metrics |
+--------------------+----------------------+--------+-------+
| Bouncer | Route | Method | Hits |
+--------------------+----------------------+--------+-------+
| caddy | /v1/decisions/stream | GET | 5508 |
| firewall@10.89.0.8 | /v1/decisions/stream | GET | 33048 |
+--------------------+----------------------+--------+-------+
+--------------------------------------------+
| Local API Machines Metrics |
+-----------+----------------+--------+------+
| Machine | Route | Method | Hits |
+-----------+----------------+--------+------+
| localhost | /v1/allowlists | GET | 5509 |
| localhost | /v1/heartbeat | GET | 5508 |
| localhost | /v1/alerts | POST | 1 |
+-----------+----------------+--------+------+
+-----------------------------------------------------------------+
| Parser Metrics |
+------------------------------------+--------+--------+----------+
| Parsers | Hits | Parsed | Unparsed |
+------------------------------------+--------+--------+----------+
| child-crowdsecurity/http-logs | 777 | 563 | 214 |
| child-crowdsecurity/sshd-logs | 90 | - | 90 |
| child-crowdsecurity/syslog-logs | 60.00k | 60.00k | - |
| crowdsecurity/caddy-logs | 259 | 259 | - |
| crowdsecurity/cdn-whitelist | 1 | 1 | - |
| crowdsecurity/dateparse-enrich | 259 | 259 | - |
| crowdsecurity/geoip-enrich | 259 | 259 | - |
| crowdsecurity/http-logs | 259 | 259 | - |
| crowdsecurity/non-syslog | 259 | 259 | - |
| crowdsecurity/public-dns-allowlist | 259 | 259 | - |
| crowdsecurity/rdns | 1 | 1 | - |
| crowdsecurity/seo-bots-whitelist | 1 | 1 | - |
| crowdsecurity/sshd-logs | 6 | - | 6 |
| crowdsecurity/syslog-logs | 60.00k | 60.00k | - |
| crowdsecurity/whitelists | 259 | 259 | - |
+------------------------------------+--------+--------+----------+
+----------------------------------------------------------------------------------------------------+
| Scenario Metrics |
+--------------------------------------+---------------+-----------+--------------+--------+---------+
| Scenario | Current Count | Overflows | Instantiated | Poured | Expired |
+--------------------------------------+---------------+-----------+--------------+--------+---------+
| crowdsecurity/http-bad-user-agent | - | 1 | 1 | 2 | - |
| crowdsecurity/http-crawl-non_statics | - | - | 81 | 185 | 81 |
| crowdsecurity/http-probing | 1 | - | 33 | 33 | 32 |
| crowdsecurity/http-sensitive-files | - | - | 4 | 10 | 4 |
+--------------------------------------+---------------+-----------+--------------+--------+---------+
+----------------------------------------------------------------------------------------------+
| Whitelist Metrics |
+------------------------------------+------------------------------------+------+-------------+
| Whitelist | Reason | Hits | Whitelisted |
+------------------------------------+------------------------------------+------+-------------+
| crowdsecurity/cdn-whitelist | CDN provider | 1 | - |
| crowdsecurity/public-dns-allowlist | public DNS server | 259 | - |
| crowdsecurity/seo-bots-whitelist | good bots (search engine crawlers) | 1 | - |
| crowdsecurity/whitelists | private ipv4/ipv6 ip/ranges | 259 | - |
+------------------------------------+------------------------------------+------+-------------+
P.S: Don’t mind the multiple firewall bouncers, the crowdsec data was saved to a remote backup, it seems like every reset of the server causes a new bouncer to show up, not a big deal (if you have an idea to fix this I’d love to see it!)
As the metrics show, journalctl is accessible to the container
vic1707@telstar:~$ podman exec crowdsec journalctl
Jul 27 18:31:09 telstar systemd[2282]: Queued start job for default target default.target.
Jul 27 18:31:09 telstar systemd[2282]: Created slice app.slice - User Application Slice.
Jul 27 18:31:09 telstar systemd[2282]: Started systemd-tmpfiles-clean.timer - Daily Cleanup of User's Temporary Directories.
Jul 27 18:31:09 telstar systemd[2282]: Reached target paths.target - Paths.
Jul 27 18:31:09 telstar systemd[2282]: Reached target timers.target - Timers.
Jul 27 18:31:09 telstar systemd[2282]: Starting dbus.socket - D-Bus User Message Bus Socket...
Jul 27 18:31:09 telstar systemd[2282]: Starting systemd-tmpfiles-setup.service - Create User Files and Directories...
Jul 27 18:31:09 telstar systemd[2282]: Listening on dbus.socket - D-Bus User Message Bus Socket.
Jul 27 18:31:09 telstar systemd[2282]: Reached target sockets.target - Sockets.
Jul 27 18:31:10 telstar systemd[2282]: Finished systemd-tmpfiles-setup.service - Create User Files and Directories.
Jul 27 18:31:10 telstar systemd[2282]: Reached target basic.target - Basic System.
Jul 27 18:31:10 telstar systemd[2282]: Starting podman-user-wait-network-online.service - Wait for system level network-online.target as user....
Jul 27 18:31:10 telstar sh[2308]: active
Jul 27 18:31:10 telstar systemd[2282]: Finished podman-user-wait-network-online.service - Wait for system level network-online.target as user..
Jul 27 18:31:10 telstar systemd[2282]: Starting CrowdsecLogs-volume.service...
Jul 27 18:31:10 telstar systemd[2282]: Starting tunnel-network.service...
Jul 27 18:31:10 telstar podman[2321]: 2025-07-27 18:31:10.34025588 +0200 CEST m=+0.094825001 system refresh
Jul 27 18:31:10 telstar podman[2337]: 2025-07-27 18:31:10.3456276 +0200 CEST m=+0.091149321 network create 0d469c08851dc2d6e0030da66e14ac2136a57b8aaa33895c54d9a1deefb147ac (name=tunnel, type=bridge)
Jul 27 18:31:10 telstar tunnel-network[2337]: tunnel
Jul 27 18:31:10 telstar podman[2321]: 2025-07-27 18:31:10.34942856 +0200 CEST m=+0.103997641 volume create CrowdsecLogs
Jul 27 18:31:10 telstar CrowdsecLogs^C-volume[2321]: CrowdsecLogs
Jul 27 18:31:10 telstar systemd[2282]: Created slice session.slice - User Core Session Slice.
Jul 27 18:31:10 telstar systemd[2282]: Starting dbus-broker.service - D-Bus User Message Bus...
Jul 27 18:31:10 telstar dbus-broker-launch[2355]: Policy to allow eavesdropping in /usr/share/dbus-1/session.conf +31: Eavesdropping is deprecated and ignored
Jul 27 18:31:10 telstar dbus-broker-launch[2355]: Policy to allow eavesdropping in /usr/share/dbus-1/session.conf +33: Eavesdropping is deprecated and ignored
Jul 27 18:31:10 telstar systemd[2282]: Started dbus-broker.service - D-Bus User Message Bus.
Jul 27 18:31:10 telstar dbus-broker-launch[2355]: Ready
Jul 27 18:31:10 telstar systemd[2282]: Created slice user.slice - Slice /user.
Jul 27 18:31:10 telstar systemd[2282]: Started podman-pause-4fc0ee5c.scope.
Jul 27 18:31:10 telstar systemd[2282]: Started podman-pause-e2d03899.scope.
Jul 27 18:31:10 telstar systemd[2282]: Finished tunnel-network.service.
Jul 27 18:31:10 telstar CrowdsecLogs-volume[2359]: Trying to pull docker.io/library/alpine:latest...
Jul 27 18:31:12 telstar CrowdsecLogs-volume[2359]: Getting image source signatures
Jul 27 18:31:12 telstar CrowdsecLogs-volume[2359]: Copying blob sha256:6e174226ea690ced550e5641249a412cdbefd2d09871f3e64ab52137a54ba606
Jul 27 18:31:12 telstar CrowdsecLogs-volume[2359]: Copying config sha256:02f8efbefad605a169e89926147edd0676646263268f303c6fb3cdfdbc4a9612
Jul 27 18:31:12 telstar CrowdsecLogs-volume[2359]: Writing manifest to image destination
Jul 27 18:31:12 telstar podman[2359]: 2025-07-27 18:31:12.65559288 +0200 CEST m=+2.215591641 container create d4650f9abedc2a8b1a70ab1eada7b2e534f39bee285e16ee875500a87f2bf45c (image=docker.io/library/alpine:latest, name=hungry_mcclintock)
Jul 27 18:31:12 telstar podman[2359]: 2025-07-27 18:31:12.63638564 +0200 CEST m=+2.196384441 image pull 02f8efbefad605a169e89926147edd0676646263268f303c6fb3cdfdbc4a9612 docker.io/library/alpine
Jul 27 18:31:12 telstar systemd[2282]: Started libpod-d4650f9abedc2a8b1a70ab1eada7b2e534f39bee285e16ee875500a87f2bf45c.scope - libcrun container.
A few more infos:
vic1707@telstar:~$ podman exec crowdsec cscli parsers list
----------------------------------------------------------------------------------------------------------------------
PARSERS
----------------------------------------------------------------------------------------------------------------------
Name 📦 Status Version Local Path
----------------------------------------------------------------------------------------------------------------------
crowdsecurity/appsec-logs ✔️ enabled 0.5 /etc/crowdsec/parsers/s01-parse/appsec-logs.yaml
crowdsecurity/caddy-logs ✔️ enabled 1.1 /etc/crowdsec/parsers/s01-parse/caddy-logs.yaml
crowdsecurity/cri-logs ✔️ enabled 0.1 /etc/crowdsec/parsers/s00-raw/cri-logs.yaml
crowdsecurity/dateparse-enrich ✔️ enabled 0.2 /etc/crowdsec/parsers/s02-enrich/dateparse-enrich.yaml
crowdsecurity/docker-logs ✔️ enabled 0.1 /etc/crowdsec/parsers/s00-raw/docker-logs.yaml
crowdsecurity/geoip-enrich ✔️ enabled 0.5 /etc/crowdsec/parsers/s02-enrich/geoip-enrich.yaml
crowdsecurity/http-logs ✔️ enabled 1.3 /etc/crowdsec/parsers/s02-enrich/http-logs.yaml
crowdsecurity/public-dns-allowlist ✔️ enabled 0.1 /etc/crowdsec/parsers/s02-enrich/public-dns-allowlist.yaml
crowdsecurity/sshd-logs ✔️ enabled 3.0 /etc/crowdsec/parsers/s01-parse/sshd-logs.yaml
crowdsecurity/syslog-logs ✔️ enabled 0.8 /etc/crowdsec/parsers/s00-raw/syslog-logs.yaml
crowdsecurity/whitelists ✔️ enabled 0.3 /etc/crowdsec/parsers/s02-enrich/whitelists.yaml
----------------------------------------------------------------------------------------------------------------------
vic1707@telstar:~$ podman exec crowdsec cscli collections list
---------------------------------------------------------------------------------------------------------------------
COLLECTIONS
---------------------------------------------------------------------------------------------------------------------
Name 📦 Status Version Local Path
---------------------------------------------------------------------------------------------------------------------
crowdsecurity/appsec-generic-rules ✔️ enabled 1.0 /etc/crowdsec/collections/appsec-generic-rules.yaml
crowdsecurity/appsec-virtual-patching ✔️ enabled 7.4 /etc/crowdsec/collections/appsec-virtual-patching.yaml
crowdsecurity/base-http-scenarios ✔️ enabled 1.2 /etc/crowdsec/collections/base-http-scenarios.yaml
crowdsecurity/caddy ✔️ enabled 0.1 /etc/crowdsec/collections/caddy.yaml
crowdsecurity/http-cve ✔️ enabled 2.9 /etc/crowdsec/collections/http-cve.yaml
crowdsecurity/linux ✔️ enabled 0.3 /etc/crowdsec/collections/linux.yaml
crowdsecurity/sshd ✔️ enabled 0.7 /etc/crowdsec/collections/sshd.yaml
crowdsecurity/whitelist-good-actors ✔️ enabled 0.2 /etc/crowdsec/collections/whitelist-good-actors.yaml
---------------------------------------------------------------------------------------------------------------------
I also tried another command I saw in the forum
vic1707@telstar:~$ podman exec crowdsec cscli explain --log "Mar 04 10:06:08 mail.domain.tld sshd[1029968]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=182.59.139.27" --type syslog -v --only-successful-parsers
line: Mar 04 10:06:08 mail.domain.tld sshd[1029968]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=182.59.139.27
├ s00-raw
| └ 🟢 crowdsecurity/syslog-logs (+12 ~9)
| └ update evt.ExpectMode : %!s(int=0) -> 1
| └ update evt.Stage : -> s01-parse
| └ update evt.Line.Raw : -> Mar 04 10:06:08 mail.domain.tld sshd[1029968]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=182.59.139.27
| └ update evt.Line.Src : -> /tmp/cscli_explain3687554181/cscli_test_tmp.log
| └ update evt.Line.Time : 0001-01-01 00:00:00 +0000 UTC -> 2025-07-31 13:46:08.386041583 +0000 UTC
| └ create evt.Line.Labels.type : syslog
| └ update evt.Line.Process : %!s(bool=false) -> true
| └ update evt.Line.Module : -> file
| └ create evt.Parsed.timestamp : Mar 04 10:06:08
| └ create evt.Parsed.timestamp8601 :
| └ create evt.Parsed.facility :
| └ create evt.Parsed.logsource : syslog
| └ create evt.Parsed.message : pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=182.59.139.27
| └ create evt.Parsed.pid : 1029968
| └ create evt.Parsed.priority :
| └ create evt.Parsed.program : sshd
| └ update evt.Time : 0001-01-01 00:00:00 +0000 UTC -> 2025-07-31 13:46:08.386087823 +0000 UTC
| └ update evt.StrTime : -> Mar 04 10:06:08
| └ create evt.Meta.datasource_type : file
| └ create evt.Meta.machine : mail.domain.tld
| └ create evt.Meta.datasource_path : /tmp/cscli_explain3687554181/cscli_test_tmp.log
├ s01-parse
| └ 🟢 crowdsecurity/sshd-logs (+8 ~1)
| └ update evt.Stage : s01-parse -> s02-enrich
| └ create evt.Parsed.sshd_client_ip : 182.59.139.27
| └ create evt.Parsed.pam_type : unix
| └ create evt.Parsed.sshd_invalid_user :
| └ create evt.Parsed.uid : 0
| └ create evt.Parsed.euid : 0
| └ create evt.Meta.log_type : ssh_failed-auth
| └ create evt.Meta.service : ssh
| └ create evt.Meta.source_ip : 182.59.139.27
├ s02-enrich
| ├ 🟢 crowdsecurity/dateparse-enrich (+2 ~2)
| ├ create evt.Enriched.MarshaledTime : 2025-03-04T10:06:08Z
| ├ update evt.Time : 2025-07-31 13:46:08.386087823 +0000 UTC -> 2025-03-04 10:06:08 +0000 UTC
| ├ update evt.MarshaledTime : -> 2025-03-04T10:06:08Z
| ├ create evt.Meta.timestamp : 2025-03-04T10:06:08Z
| ├ 🟢 crowdsecurity/geoip-enrich (+13)
| ├ create evt.Enriched.ASNOrg : Mahanagar Telephone Nigam Limited
| ├ create evt.Enriched.IsInEU : false
| ├ create evt.Enriched.ASNumber : 17813
| ├ create evt.Enriched.IsoCode : IN
| ├ create evt.Enriched.Latitude : 19.074800
| ├ create evt.Enriched.Longitude : 72.885600
| ├ create evt.Enriched.SourceRange : 182.56.0.0/14
| ├ create evt.Enriched.ASNNumber : 17813
| ├ create evt.Meta.IsoCode : IN
| ├ create evt.Meta.SourceRange : 182.56.0.0/14
| ├ create evt.Meta.ASNNumber : 17813
| ├ create evt.Meta.ASNOrg : Mahanagar Telephone Nigam Limited
| ├ create evt.Meta.IsInEU : false
| ├ 🟢 crowdsecurity/public-dns-allowlist (unchanged)
| └ 🟢 crowdsecurity/whitelists (unchanged)
├-------- parser success 🟢
├ Scenarios
├ 🟢 crowdsecurity/ssh-bf
├ 🟢 crowdsecurity/ssh-bf_user-enum
├ 🟢 crowdsecurity/ssh-slow-bf
└ 🟢 crowdsecurity/ssh-slow-bf_user-enum