Hello everyone
I have a caddy + Coraza + Crowdsec with docker compose working fine and reporting to the console.
My OS is raspian which is based on Debian 12 (bookworm)
I have decided to add the FW bouncer so that the IPs are blocked in the system FW, which is an nftables.
I have installed the nftables version on the OS directly and connected it to crowdsec.
When I force a block on Coraza, the Crowdsec integration parses the log, detects it and blocks it.
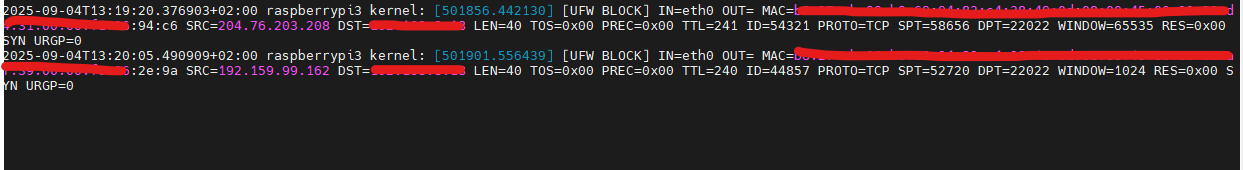
I see that the blocked IP is added to the blacklist of the FW bouncer but I don’t see anything in the kern.log and that makes me suspect that something is not working well because I do see all the UFW entries.
I’ll give you my configuration, the doubts I’ve had and the logs to see if you can tell me the error or confirm that it is working well.
Do you think so?
Host information

Logs and cscli commands
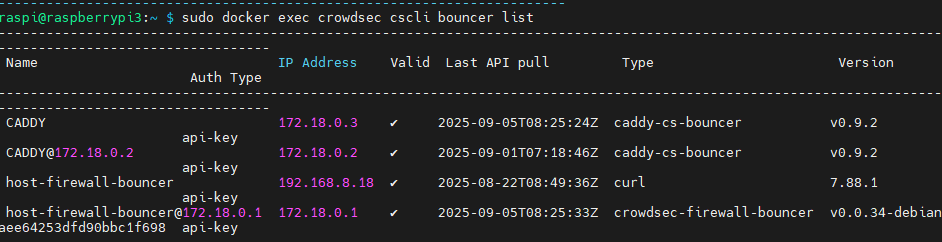
Bouncer list
When I force a Coraza Block and when I manully add a ban:
Note: I’m behind Cloudflare tunnel and I see in caddy.log the access from the same IP (172.18.0.1).
Usually I have 172.18.0.0/12 in the whitelist but I remove it to test.
crowdsec.log
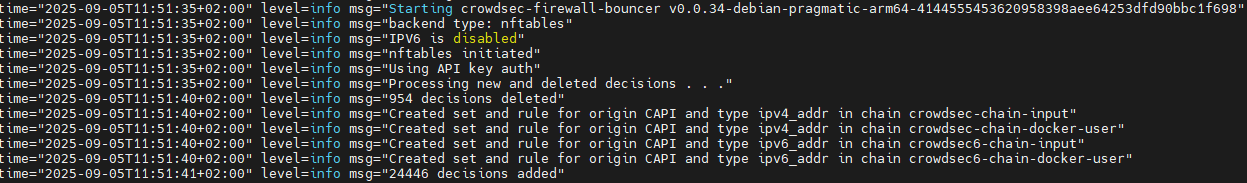
crowdsec-firewall-bouncer.log
![]()
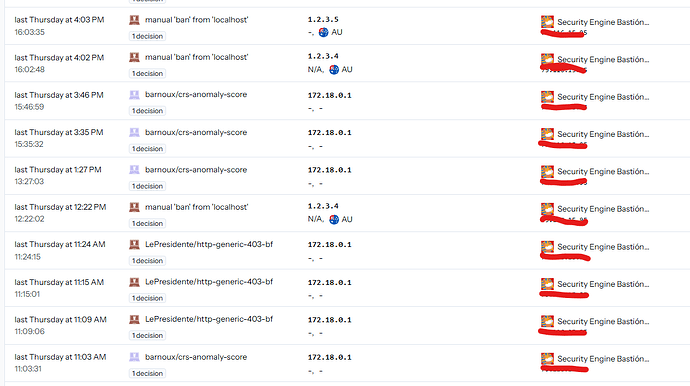
decision list

nft list table crowdsec
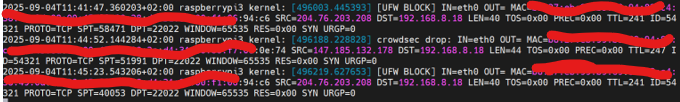
kern.log => Nothing
According to what I have read in forums, you should see posts like these
Journalctl => also nothing
In both cases I see the decisions in the decision list and the app.crowdsec console is informed.
Configuration files
mode: nftables
update_frequency: 10s
log_mode: file
log_dir: /var/log/
log_level: info
log_compression: true
log_max_size: 100
log_max_backups: 3
log_max_age: 30
api_url: http://localhost:8080/
api_key:XXXXX
## TLS Authentication
# cert_path: /etc/crowdsec/tls/cert.pem
# key_path: /etc/crowdsec/tls/key.pem
# ca_cert_path: /etc/crowdsec/tls/ca.crt
insecure_skip_verify: false
disable_ipv6: true
deny_action: DROP
deny_log: true
supported_decisions_types:
- ban
#to change log prefix
#deny_log_prefix: "crowdsec: "
#to change the blacklists name
blacklists_ipv4: crowdsec-blacklists
blacklists_ipv6: crowdsec6-blacklists
#type of ipset to use
ipset_type: nethash
#if present, insert rule in those chains
iptables_chains:
- INPUT
# - FORWARD
- DOCKER-USER
iptables_add_rule_comments: true
## nftables
nftables:
ipv4:
enabled: true
set-only: false
table: crowdsec
chain: crowdsec-chain
priority: -10
ipv6:
enabled: true
set-only: false
table: crowdsec6
chain: crowdsec6-chain
priority: -10
nftables_hooks:
- input
# - forward
- docker-user
# packet filter
pf:
# an empty string disables the anchor
anchor_name: ""
prometheus:
enabled: false
listen_addr: 127.0.0.1
listen_port: 60601
Regarding this configuration, I have not found documentation.
They came in the file after installation and what I did was adapt it to the IP tables, which are documented.
I added docker-user because I read that if you have crowdsec in docker you have to do it.
I have many doubts about this because in addition the CHAINs in iptables are uppercase and here it was filled in lowercase and I don’t know if I have to change it.
nftables_hooks:
- input
# - forward
- docker-user
The same with the priority parameter that were already configured at -10 in the original file.
startup log
Summing up.
I don’t know if the FW bouncer configuration for nftables_hook is correct and I also don’t know if it is communicating well with crowdsec and nftables because I don’t see anything being written in the kern.log.
On the other hand.
is there any way to log the source IP instead the FW bouncer IP (172.18.0.1)?
I hope I have explained myself well.
If you need more information I am fully available.
thank you very much in advance.